In this article, we will be deploying a Java Spring Boot Application on Kubernetes.
Here’s a high-level overview of the process of deploying a Spring Boot application on Kubernetes:

- Containerize the Spring Boot Application
- Create Kubernetes Deployment
- Define Kubernetes Services
- Deploy the Application to Kubernetes Cluster
Setups:
GitHub Repo for source code:
https://github.com/HARSHALJETHWA19/springboot-k8s.gitSetup :
Launch an instance from an Amazon Linux 2 or Amazon Linux AMI
with t2.medium
2. Connect to your instance.
3. Update the packages and package caches you have installed on
your instance.
yum update -y
Docker Service :
yum install docker -y
docker -vStart the Docker service
systemctl start docker
systemctl enable dockerInstall Conntrack and git:
yum install conntrack -y
yum install git -yInstall Kubernetes(k8) :
curl -LO
https://storage.googleapis.com/minikube/releases/latest/minikubelinux-
amd64
sudo install minikube-linux-amd64 /usr/local/bin/minikubeStart Minikube :
minikube start --force --driver=docker
minikube version
Install kubectl :
sudo curl -LO "https://dl.k8s.io/release/$(curl -s https://storage.googleapis.com/kubernetes-release/release/stable.txt)/bin/linux/amd64/kubectl"
sudo chmod +x kubectl
sudo mv kubectl /usr/local/bin/Clone the repo :
cd /opt/
git clone https://github.com/HARSHALJETHWA19/springboot-k8s.gitMake the Database UP:
cd springboot-k8s
kubectl create -f db-deployment.yaml
kubectl get pods
kubectl exec -it mysql-79554598b8-rqzj8 -- /bin/bash
mysql -u root -p root
show databases;
Maven Install :
yum install maven -yCreate the docker image :
docker build -t harshal1903/springboot-crud-k8s:1.0 .
docker login
[ CREATE A DOCKER HUB ACCOUNT BEFORE ]
Give dockerhub username and password
docker image push harshal1903/springboot-crud-k8s:1.0
kubectl apply -f app-deployment.yaml
kubectl get svc
minikube ip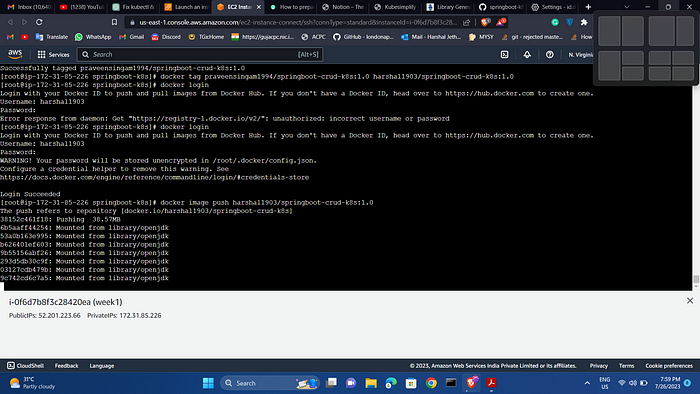
PUT PORT FORWARD :
kubectl port-forward --address 0.0.0.0 svc/springbootcrud-
svc 8080:8080 &[HOST PORT TO CONTAINER PORT]\
kubectl port-forward --address 0.0.0.0 svc/{your service name}
{external port to the Internet}:{your service port, the port your app is
listening on in it's container}
for example, if my service is named store and is listening on 80
kubectl port-forward --address 0.0.0.0 svc/store 8888:80
JSON DATA TO BE HITTED WITH POST :
URL POST — http://<EC2IP>:8080/orders
Check Database
URL GET — http://<EC2IP>:8080/orders/1


FOR DASHBOARD:
/usr/local/bin/kubectl proxy — address=’0.0.0.0' — accept-hosts=’^*$’
IN OTHER TERMINAL
minikube dashboard

20 — Hit this url in browser
http://<EC2IP>:8001/api/v1/namespaces/kubernetesdashboard/
services/http:kubernetesdashboard:/
proxy/#/pod?namespace=default